Caveats: this worked for me, but your mileage may vary. I'm using 10.2.5, and I haven't tried it with other sub-versions. It should work with 10.2.
10.2 uses a variant of MIT's kerberos, so what we're going to do is install some bits from MIT, configure kerberos for our domain, then install a plug in to get afs token, and finally set up login authorization to generate tickets from the main GUI login window
You can get MIT's Kerberos Extras from:
http://web.mit.edu/macdev/Development/MITKerberos/Common/Documentation/osx-kerberos-extras.html
Installation of this will enable kerberos support for Carbon applications, and set up a sample kerberos configuration file. It's really an optional step, but why not?
Once it's installed, go to /Library/Preferences and find the edu.mit.Kerberos file. As root, or using sudo, make a backup, then open this file with a text editor (eg. vi, pico, BBEdit). For default realm, use your main kerberos realm. If you're in a Kerberos4 realm, add the data in the "v4" sections. For more detailed information, see the MIT Kerberos for OS X preferences and faq pages.
If you also want to get AFS tokens when you login add a line in [libdefaults] for 'login_logout_notification = "aklog"', this will create the link to kfm_aklog plugin we'll install in Step 3. If you get an AFS token on login, you can access your AFS space without having to go to the terminal window and typing running aklog. Of course, this presupposes that you've installedan AFS client and have configured your machine to access an AFS cell.
In this first example below, I've put the information for the kerberos authentication servers for the two afs cells I use, isis.unc.edu and cs.unc.edu.
[libdefaults]
login_logout_notification = "aklog"
default_realm = CS.UNC.EDU
ticket_lifetime = 600
noaddresses = TRUE
dns_lookup_realm = false
dns_lookup_kdc = false
[realms]
ISIS.UNC.EDU = {
kdc = krb0.unc.edu.:88
kdc = krb1.unc.edu.:88
kdc = krb2.unc.edu.:88
admin_server = krb0.unc.edu
default_domain = isis.unc.edu
}
[domain_realm]
.isis.unc.edu = ISIS.UNC.EDU
isis.unc.edu = ISIS.UNC.EDU
[v4 realms]
CS.UNC.EDU = {
kdc = kerberos.cs.unc.edu
kdc = kerberos-1.cs.unc.edu
kdc = kerberos-2.cs.unc.edu
admin_server = kerberos.cs.unc.edu
default_domain = cs.unc.edu
string_to_key_type = afs_string_to_key
}
ISIS.UNC.EDU = {
kdc = krb0.unc.edu.
kdc = krb1.unc.edu.
kdc = krb2.unc.edu.
admin_server = krb0.unc.edu.
default_domain = isis.unc.edu
string_to_key_type = mit_string_to_key
}
[v4 domain_realm]
.cs.unc.edu = CS.UNC.EDU
cs.unc.edu = CS.UNC.EDU
isis.unc.edu = ISIS.UNC.EDU
.isis.unc.edu = ISIS.UNC.EDU
Isis users should try the following in the same file, it's the same file without the settings for the CS.UNC.EDU realm. In theory, you shouldn't need the v4 data, but things seem to work better with it in place.
[libdefaults]
login_logout_notification = "aklog"
default_realm = ISIS.UNC.EDU
ticket_lifetime = 600
noaddresses = TRUE
dns_lookup_realm = false
dns_lookup_kdc = false
[realms]
ISIS.UNC.EDU = {
kdc = krb0.unc.edu.:88
kdc = krb1.unc.edu.:88
kdc = krb2.unc.edu.:88
admin_server = krb0.unc.edu
default_domain = isis.unc.edu
}
[domain_realm]
.isis.unc.edu = ISIS.UNC.EDU
isis.unc.edu = ISIS.UNC.EDU
[v4 realms]
ISIS.UNC.EDU = {
kdc = krb0.unc.edu.
kdc = krb1.unc.edu.
kdc = krb2.unc.edu.
admin_server = krb0.unc.edu.
default_domain = isis.unc.edu
string_to_key_type = mit_string_to_key
}
[v4 domain_realm]
isis.unc.edu = ISIS.UNC.EDU
.isis.unc.edu = ISIS.UNC.EDU
Save the file. You will have to logout and log back in to test it, but a reboot shouldn't be required (Note: you can also put this file in your home /Library/Preferences folder--Kerberos will check your folder first, and then look in the system folder.)
![]() Once you're logged back in, look in
/Applications/Utilites for the Kerberos application--the MIT
extras install puts an alias to this where you can find it,
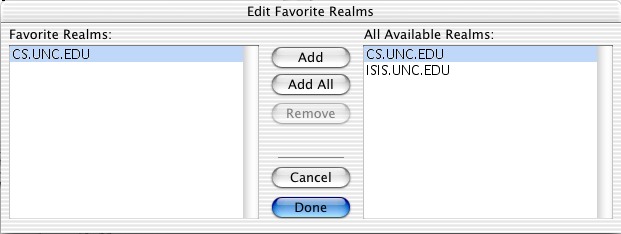
instead in CoreServices. Open this, and go to Edit, Edit
Favorite Realms, and add the cs.unc.edu realm.
Once you're logged back in, look in
/Applications/Utilites for the Kerberos application--the MIT
extras install puts an alias to this where you can find it,
instead in CoreServices. Open this, and go to Edit, Edit
Favorite Realms, and add the cs.unc.edu realm.
Once you've done that, you should be able to use the main window to get kerberos tickets.
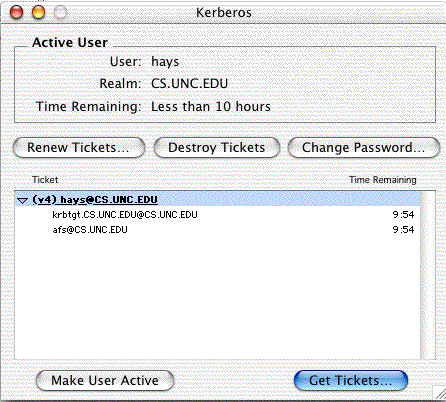
So far so good--now you should be able to use applications that know how to use kerberos. At UNC, that doesn't mean much, since we don't use kerberos all that much and most applications aren't kerberized. But this does lay the groundwork for the next step, which is automatically getting AFS tokens for access to your online file space.
This plugin will obtain an AFS token for you on login, and destroy it on logout. You can download the source from Alexei Kosut's page, but I've also made a binary available here. I think the binary will work, please let me know if it doesn't. As root or via sudo, make a directory named /Library/Kerberos Plug-Ins, and then copy the kfm_aklog.tgz file into it. Unpack the file, and then delete the compressed version:
sudo mkdir /Library/Kerberos\ Plug-Ins cd /Library/Kerberos\ Plug-Ins sudo curl -O http://www.ibiblio.org/macsupport/kerberos/kfm_aklog.tgz sudo gnutar -xzf kfm_aklog.tgz sudo rm kfm_aklog.tgz
This step is from http://docs.info.apple.com/article.html?artnum=107154. From a terminal windos, su to root or use sudo to open /etc/authorization in a text editor, and finde the system.login.done key in the file. Change <string>switch_to_user</string> to <string>switch_to_user,krb5auth:login</string>, and save the file. This will cause the mac to pass your userid and password to the kerberos system on login, and if that's successful, you'll get a ticket granting ticket from kerberos that will let Alexei's plugin to get an AFS token when you login.
<key>system.login.done</key>
<dict>
<key>eval</key>
<string>switch_to_user,krb5auth:login</string>
</dict>
<!-- krb5auth:login can be used to do kerberos authentication as a
side-effect of logging in. Local username/password will be used. -->
Logout and login again, and then open the Kerberos utility or run klist to see that you have tickets. Then try to access your afs space, or open a terminal window and type the "tokens" command to see that you have AFS tokens.
What this procedure does (assuming I'm understanding all of it correctly) is set up the GUI's login window to try to get a Kerberos ticket when you login by passing the same userid and password to the kerberos server. When this is successful, you are given kerberos tickets to the default realm. If you've added the login_logout_notification = "aklog" line to the edu.mit.kerberos file, Alexei's kfm_aklog plugin will be called when you get that Kerberos ticket, and will get you an AFS token.